Microsoft Graph Token-based Authentication
Service Provider access to Hosted Essentials Plus or Hosted Pro license customers' Microsoft 365 platform must now always be secured using Microsoft Graph Token-based authentication as a result of enhanced Microsoft security policies. The connection can be secured using the following methods:
|
■
|
Password-based and Token-based authentication: A Microsoft Graph access token is claimed based on the user name and password provided by the customer tenant. Using this method, Service provider uses both the customer's user and password and generated token to access the customer's M365 platform. |
|
■
|
Token-based authentication only: A Microsoft Graph access token is claimed directly. Using this method, the Service Provider uses only the generated token to access the customer's M365 platform. This is the recommended the method. |
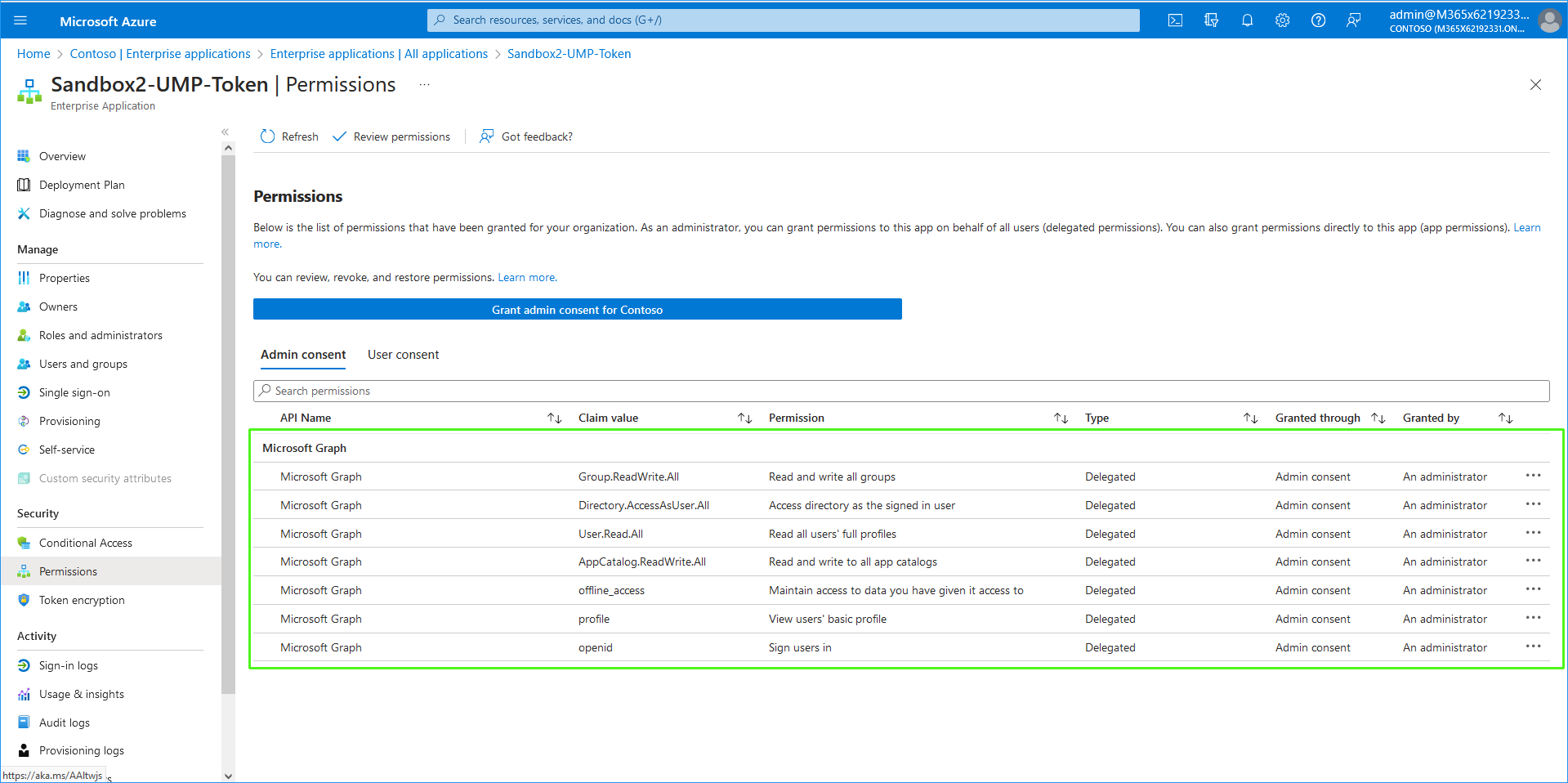
Once consent is provided, an Enterprise application is created on the customer Azure tenant with the following permissions:
|
■
|
Access Microsoft Teams and Skype for Business as the signed in user |
|
■
|
Read and write all groups |
|
■
|
Access directory as the signed-in user |
|
■
|
Read all users' full profiles |
|
■
|
Read and write to all app catalogs |
|
■
|
Maintain access to data you have given it access to |
Queued tasks will not be synchronized with the customer's Microsoft 365 platform until token-based authentication is implemented and the connection is successfully verified.
Admin consent must be provided for the permissions shown below.
The AadGraph and MsGraph scopes have been removed from the Token Onboarding process.
